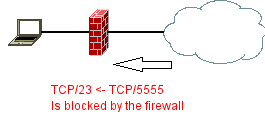
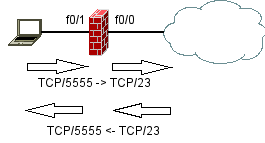
When devices should be synced, it’s time to configure ntp with sources, servers and clients/peers.
Every cisco router can act as the ntp master.
ntp master 1
is just everything you need to configure the router as an ntp source. The router will use 127.127.7.1 address as the local source for ntp updates. This is a reference clock for the NTP protocol to be used as the source of time. This is mostly a radio clock or some other kind of clock sometimes even attached directly to the router.
R1#show ntp associations detail
127.127.7.1 configured, our_master, sane, valid, stratum 0
As of IOS 12.1 there are two reference clock drivers for ntp:
R1(config-line)#ntp refclock ?
telecom-solutions Telecom Solutions GPS
When devices should be synced, it’s time to configure ntp with sources, servers and clients/peers.
Every cisco router can act as the ntp master (here with stratum 1).
ntp master 1
is just everything you need to configure the router as an ntp source. The router will use 127.127.7.1 address as the local source for ntp updates. This is a reference clock for the NTP protocol to ne used as the source of time. This is mostly a radio clock or some other kind of clock sometimes even attached directly to the router.
R1#show ntp associations detail
127.127.7.1 configured, our_master, sane, valid, stratum 1
As of IOS 12.1 there are two reference clock drivers for ntp:
R1(config-line)#ntp refclock ?
telecom-solutions Telecom Solutions GPS
trimble Trimble Navigation TSIP Protocol
So it’s possible to have an external clock hooked up to the aux port. Trimble has a „Acutimeâ„¢ Gold GPS Smart Antenna“ with an RS422 port. Don’t know if it’s still possible to use this antenna with the 7200.
So if you use the 127.127.7.1, the local ntp timer, as the master with
ntp master 1
you can also configure the stratum for this clock. In the hierarchal ntp model, where server and clients distribute time to another, the stratum value will give information on how far the original clock is away. Stratum 0 is a real time source, like an external gps or dcf77 receiver. Stratum 1 is normaly a host which uses it’s local clock as a time source, like the „ntp master“ command does. Every client in between adds a stratum and inaccuracy with about 10-100 ms. So the higher stratum values indicate a better time source regarding accuracy.
Access to the NTP service is controlled with the
„ntp access-group“
command.
ntp access-group knows the following options (from the documentation).
The access group options are scanned in the following order, from least restrictive to most restrictive:
1. ![]() peer—Allows time requests and NTP control queries and allows the system to synchronize itself to a system whose address passes the access list criteria.
peer—Allows time requests and NTP control queries and allows the system to synchronize itself to a system whose address passes the access list criteria.
2. ![]() serve—Allows time requests and NTP control queries, but does not allow the system to synchronize itself to a system whose address passes the access list criteria.
serve—Allows time requests and NTP control queries, but does not allow the system to synchronize itself to a system whose address passes the access list criteria.
3. ![]() serve-only—Allows only time requests from a system whose address passes the access list criteria.
serve-only—Allows only time requests from a system whose address passes the access list criteria.
4. ![]() query-only—Allows only NTP control queries from a system whose address passes the access list criteria.
query-only—Allows only NTP control queries from a system whose address passes the access list criteria.
If you want to update from a local router (software) clock, you have to include the 127.127.7.1 address in the access-list statement also.
ntp master 1
ntp access-group peer 10
access-list 10 permit 127.127.7.1
Otherwise the local clock will not be able to synchronize.
If you want to get time from a remote server 1.1.1.1 and allow only 2.2.2.2 to get time from you:
ntp server 1.1.1.1
ntp access-group peer 1
access-list 1 permit 2.2.2.2
Source:
http://www.cisco.com/en/US/docs/ios/12_1t/12_1t1/feature/guide/dtrimble.html
http://www.cisco.com/en/US/products/sw/iosswrel/ps1818/products_tech_note09186a008015bb3a.shtml